Based on the title of this post, you might be expecting some futuristic revelations about passwords and how quickly they'll be going away. If that's what you're looking for, look at the technical blogs of high-tech companies with futuristic visions that generally fall flat. The conversation about passwords that has been ongoing in industry is an interesting one we've been watching from the sidelines but not publicly commented on until now. Now that the idea of potentially going password-less has gained some prominence among average users, some good common sense insight into this issue is warranted.
Phasing out passwords has been the wet dream of many in the tech industry for some time now. A Microsoft white paper from 2016, titled The Quest to Replace Passwords: A Framework for Comparative Evaluation of Web Authentication Schemes" takes a deep-dive into the issue, as if passwords were akin to oil, a dirty and allegedly "obsolete" technology that must be phased out be "clean" and "superior" authentication technology. A key problem is that much of the argument of password-haters is incredibly subjective, biased, or assuming.
First, let's clear up a few myths surrounding passwords:
- Passwords Are Insecure. This is probably the driving force behind efforts to replace passwords. The problem is, well, this isn't true. Passwords themselves are not inherently insecure. Rather, the way that many people approach, use, or store passwords is insecure. Passwords, if you use them properly, are actually very secure. The insecurity that exists in passwords today stems entirely from user error — if your password is "password" or "abc123", well, no duh, you shouldn't be using that to protect your banking information. Passwords are neutral. If you want a secure password, you can have one. If you want an insecure one, well, nobody's stopping you (although it seems nowadays many systems will insist you use half the symbols in the alphabet and a series of Wingdings symbols to adequately "protect yourself")… more on this in the next point. Apart from user error, there's been no shortage of data breaches in recent years that have resulted in account compromises. However, passwords, once again, are not the problem. Astonishingly, vendor and programmer stupidity are. In many, perhaps most, of these breaches, whenever credentials have been compromised it is because they were in the database as plain text Yikes! There is absolutely no reason to not be salting and hashing your passwords today! Seriously, even a third-grader can do it thanks to PHP's password_hash and password_verify functions. If a third grader can do it, multinational companies can, too!
- Password Security Means Complexity. This might be one of the more detrimental myths, because it's responsible for the aggrivatingly common "complexity requirement" that many sign-up forms will insist upon these days. It's becoming more and more common for passwords to have to contain lowercase letters, uppercase letters, numbers, and symbols! The reality is this guideline is simply misguided. Password security is determined largely by entropy, and when it comes entropy, length trumps complexity, by far. This famous XKCD comic sums it up pretty nicely:

In other words, passwords that are hard for us to remember are easy for computers to guess. And guess what? Long passwords that are easy for us to remember are hard for computers to guess. Go figure.
What's the takeaway? Screw password complexity. Use an adequately long password and (provided you use common sense), your password is effectively uncrackable. Password complexity enforcers, unfortunately, do us all a big disfavor by encouraging, albeit perhaps inadvertently, shorter passwords that are less secure. At least they don't yet insist we also incorporate ALT characters into our passwords. Better hope every computer you use for the rest of your life has a full-size keyboard…
Here's a brief aside to comment on the use of now-insecure MD4 hashing for Windows passwords. Your Windows password may be compromisable if you use a short password, even if it's complex. Use an adequately long password, though, and you can sleep better at night. It's really not that difficult:
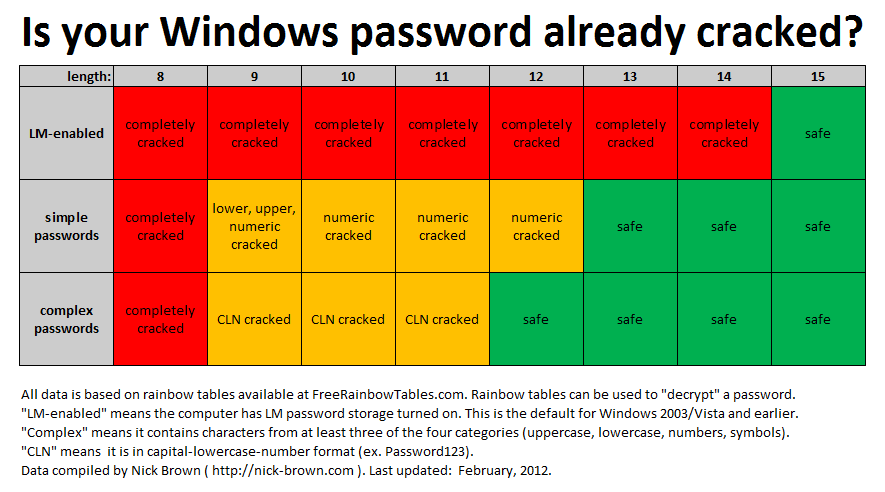
- Passwords Are Outdated. This is the driving force between much unnecessary and detrimental change (misleadingly called innovation) in the technology sector. Well, if ain't broke, don't fix it. Just because something has been in use for a long time is not a valid reason to changes things up for no reason. It's a lesson that software companies and many others in the tech industry would do well to learn. The truth is, despite claims to the contrary, passwords work remarkably well for a number of reasons and no alternative comes closer to being even half as good as what we already have.
- Two-Step/Two-Factor Authentication Increases Security. This really depends, but it's not necessarily true, and sometimes it's blatantly false. If your idea of two-step authentication is receiving an SMS text, you can pretty much say goodbye to any notion of security there. If you're doing something that's at least "corporate grade" like using an RSA token, you're seeing prettier. At the same time, two-factor authentication on its own is no guarantee of security. If you leave your RSA token on your desk all the time, it's the same as writing your password on a sticky note and pasting it on the monitor. Personally, we're not fans of two-factor authentication. There are valid use cases for it, but the inconvenience and inaccessibility of it is only rarely enough to compensate for the additional security it could afford, and even then, only if done and used properly.
More could be said about passwords, but these are the important points. Passwords are not inherently insecure. Any insecurity that results from the use of passwords is entirely due to user carelessness (or downright stupidity) or irresponsible storage of passwords (which boils down to programmer stupidity, really).
Let's return to the Microsoft whitepaper mentioned above. The problem with white papers like this and other technologists who believe in a password-free future is they don't see reality as it is, only as it exists for them. The Microsoft whitepaper makes several generalizing statements that are just downright stereotypical, discriminatory, and assuming. On page 2, here is one of the criteria used to evaluate password alternatives:
U3 Nothing-to-Carry: Users do not need to carry an additional physical object (electronic device, mechanical key, piece of paper) to use the scheme. Quasi-Nothing-to-Carry is awarded if the object is one that they’d carry everywhere all the time anyway, such as their mobile phone, but not if it’s their computer (including tablets).
Clearly, this is ridiculous. Quasi-Nothing-to-Carry? No. Mobiles do not qualify as Nothing-to-Carry, nor do they qualify as Quasi-Nothing-to-Carry. Consider that not everyone has a mobile and many people have no interest in owning or using one. Consider that they are often easily misplaced or forgotten even by those who do own them. The "Quasi-Nothing-to-Carry" category does not exist. Suggesting otherwise is a downright priviledged, ignorant, and exclusionary delusion.
It would hardly be a technology white paper without more of these short-sighted comments. The ignorance and downright infuriatingly baseless comments only get worse from there. Here is an excerpt from page 9:
On deployability: it’s Quasi-Accessible insofar as most disabled users, including blind people, can use a mobile phone too (note the user doesn’t need to transcribe codes from the phone). We assume most users will already have a phone, though perhaps not one of the right type (with Java, Bluetooth etc), hence it has Quasi-Negligible-Cost-per-User.
This is an incredibly delusional and reckless statement, and it could not be further from the truth.
The false make-believe idea that many disabled can use a mobile phone is completely false. Many people, in fact, are disabled by this very technology. To pretend that this technology is friendly and accessible to the disabled is not just ignorant, but downright dangerous, as this false belief could easily be used to effectively "disenfranchise" the disabled from technology. Indeed, even for a normal person that isn't disabled, mobiles are hardly accessible technology. But for the disabled, a mobile can be downright debilitating.
Further infuriating is the assumption that people who do own phones more or less own smartphones. Let's set aside the fact that this precisely the type of "phone" that is least accessible to the disabled and impaired. The implied assertion that all phones are mobiles, when in reality, the prototypical phone is a landline telephone, is just plain wrong, end of story. The discussion here completely ignores "regular" phones, whether they be traditional landlines or VoIP. Here, the author assumes that most people have phones, and that they have mobile phones, at the very least, if not "smart" phones. The idea that anyone could own a landline does not even come up here. This is the same kind of disgusting shortsighted discrimination that misleads many websites into thinking it's "OK" to send a text message without an an accessible alternative, such as a phone call or an email. The telephone was invented for talking. If you're asking for a phone number, that number should not be used for anything but calling it. Somehow, major tech companies still haven't figured out that you can't text a telephone.
The last falsehood spewed in this sentence is also worrisome… "Quasi-Negligible-Cost-per-User". What a privileged, ignorant, and assuming lie. I suppose if you're a millionaire, you wouldn't think twice about dropping a grand on the epitome of planned obsolescence every two years. Apparently, the idea that poor people exist — who have better things to pay for than iPhones that will either stop working or become obsolete in a couple years — has not occurred to these others. Far from being inclusive, the authors instead perpetuate myths about technology that discriminate against the most vulnerable people for whom technology was supposed to make life easier — the disabled, the poor, the elderly, and by extension, all people in general.
The Microsoft white paper is from 2016, by which time Microsoft had already sold itself ought, so it's not entirely surprising that the white paper is really just elite technologists describing the world they live in, rather than the world that actually exists. At the same time, companies like Microsoft are largely responsible for changes and "innovation" in the technology sector, so it's a bit disturbing to see claims that border on the verge of "Holocaust-denier" from such a company.
Clearly, Microsoft can't be trusted to report the truth about the ways that passwords and their alternatives actually affect people (then again, we can't trust them to make software anymore, either). Unsurprisingly, companies like Microsoft conveniently fail to discuss the shortcomings of password alternatives and portray them instead as some magical holy grail solution (which they actually aren't), when really, most current security problems could simply be solved by more responsible choices about password usage and password storage. Instead, the tech industry wants to solve a problem that doesn't exist, even if it means effectively disenfranchising entire groups of people in the process. Ouch.
The fact of the matter is that passwords are here to stay. The reason why is that passwords possess many properties that make them quite difficult (arguably impossible) to replace. Here's what those pushing their own post-password agendas won't tell you:
- Passwords are easy. Passwords are easy to use. It probably takes most people a couple seconds to unlock their computer when they come back to it (even with a lengthy and secure password). In recent years, we've seen a variety of options emerge to supplement passwords, like biometric sensors, facial recognition, and even methods as playful as drawing on your touchscreen (let's set aside the fact that most monitors are not, and will likely never be, touchscreen). Biometric sensors have actually been around for a while, but Windows 10 also lets you use facial recognition and drawing to supplement passwords (supplement, because you still have a password, but can use an alternative method to log in or unlock). While it's your own fault if you type in your password wrong (and usually if you do, let's face it, it's because you forgot to turn off CAPS LOCK), there's no shortage of things that can go wrong when trying to use a webcam or touch screen to log in.
- Passwords are accessible. Unless you're missing a limb, you probably have little difficulty typing a password. And all you need to type a password is a keyboard, which is ubiquitous across computers today. The thought of a workstation without a keyboard is almost unfathomable. Yet, the reality is most computer monitors don't have built-in cameras (and rightly so), and people who do not otherwise have a need for a webcam will not feel compelled to get one solely so they can log in to their computer by smiling at it. There is no reasonable expectation that most (let alone all) computers now or in the future will have cameras, microphones, or other biometric sensors. Indeed, most of these can only be found on laptops. If you have a standard desktop computer, it's expected that you connect peripherals separately, and thus you have what you need and not what you don't need.
Passwords, because they boil down to text, are also thus uniquely able to transcend pretty much every hardware barrier imaginable. You can log in to a remote computer using RDP with a password. Once logged in, you can log in to any website or application — again, using a password. Heck, you can even log in to a remote system using a teletypewriter — using a password! Prior to graphical operating systems like Windows, computers only worked with text. Password alternatives fail miserably because they're simply not compatible with 50+ years of computing technologies, all of which can work with text, but perhaps not much else. - Passwords are secrets, not properties. Passwords work well because they are secrets. You don't need to be you to log in, you need to know the secret. While some may see this as a disadvantage, it's really not, as it's not difficult at all to keep a secret, well, secret. There are, however, legitimate reasons for sharing passwords. How do you propose to easily associate the face of everyone authorized to use a system using a certain account? If you come up with a solution, I can guarantee it's less elegant than having one password that is simply shared with the appropriate parties.
Furthermore, as the majority of passwords are not meant to be shared, keep in mind that the conception of a password as a shareable secret has tremendous implications for anonymity and privacy. Most password alternatives, by design, invade your privacy and do not allow anonymity.
What it really comes down to is the ability to provide and accept passwords is universally supported by all computer systems. The same simply cannot be said of any of password alternatives. Let's face it — passwords may suck, but all the password alternatives suck even more. Like QWERTY keyboards, passwords, love 'em or hate 'em, are here to stay.